Your plate is full.
You’re iterating and perfecting your products. You’re making sure your customer experience is top-notch, and that your user experience is seamless. You’re planning out your BFCM strategies.
And then, a well-meaning employee clicks on a link in a (seemingly) innocent email—and, in the process, unwittingly becomes the victim of a cyberattack.
All of a sudden, you’ve got a four-alarm fire to put out.
The good news is that you’re not alone. According to a report Kapersky released in early 2022, there were 3B more cybersecurity attacks on consumers compared to the same time period in 2021.
And while cybersecurity attacks are clearly on the rise, a positive outcome of this increasing threat is that the cybersecurity community is working hard to increase both awareness and action––including here at Klaviyo.
In honor of Cybersecurity Awareness Month this October, read on to learn more about the ways your company may be vulnerable—and how you and your team can protect your Klaviyo account.
The types of cyberattacks to watch out for
Social engineering is when bad actors manipulate people into sharing confidential or personal information that can then be used for fraudulent purposes.
For example, let’s say you get an email, a text, or even a phone call from someone high up at your company. You recognize the name, and the request—to buy $500 worth of gift cards for a partner event— sounds reasonable enough. Even the phone call—if it happens—seems legitimate.
You buy the gift cards with urgency, as requested. You submit paperwork to be reimbursed, but nothing comes through when you get your next paycheck.
You reach out to the person who requested that you buy the gift cards, and they have no idea what you’re talking about.
What happened?
You got socially engineered. Even worse, you got “spearphished”—when a bad actor targets a specific person (in this case, you).
You go back to the email or text request to double check and realize that the sender’s information is just a little bit off from the person’s who they were trying to imitate.
All sorts of new and developing technology is making this type of attack—a business identity compromise (BIC)—easier to commit and more difficult to spot.
Here are a couple of examples:
- Social media can tell a bad actor the names of people you’re close with. Then, they can reference a third party you know in common, which may help build rapport with you.
- Deepfakes and voice cloning make attacks even more believable by allowing attackers to create videos or audio of company leaders saying certain things.
In 2021, the FBI put out a notice warning that BIC attacks will increase in frequency as the technology to make them becomes more widely available.
There are several types of social engineering cyber attacks, including:
- Phishing (both email and SMS)
- Whaling
- Diversion theft
- Baiting
- Pre-texting
- Scareware
- Tailgating / Piggybacking
- Watering hole
Let’s look at each.
Phishing
Phishing is a common form of cyberattack. It is one that is specifically targeted to steal information like log-in credentials or sensitive data. It’s often disguised as a credible email.
The first known phishing attempt occurred in 1996, as hackers pretended to be AOL administrators and phished for log-in credentials so they could access the internet for free.
More than two decades later, phishing is extremely common, and a practice that all online users must be vigilant about.
“If you wonder why criminals phish, it is because email is where their targets are reachable. And while only 2.9% of employees may actually click on phishing emails, a finding that has been relatively steady over time, that is still more than enough for criminals to continue to use it,” writes Verizon in its annual breach investigation report.
Whaling
Whaling is a common variation of phishing that targets business executives. These types of cyber attacks usually spoof the email addresses of other high-ranking employees in the company and contain urgent messaging about a fake emergency or time-sensitive opportunity.
For example, your CFO may get an urgent email seemingly from your CEO—asking them to quickly review data at a specific link provided. If your CFO were to click that link, they could then expose a lot of confidential, sensitive information due to their higher level at the organization.
Diversion theft
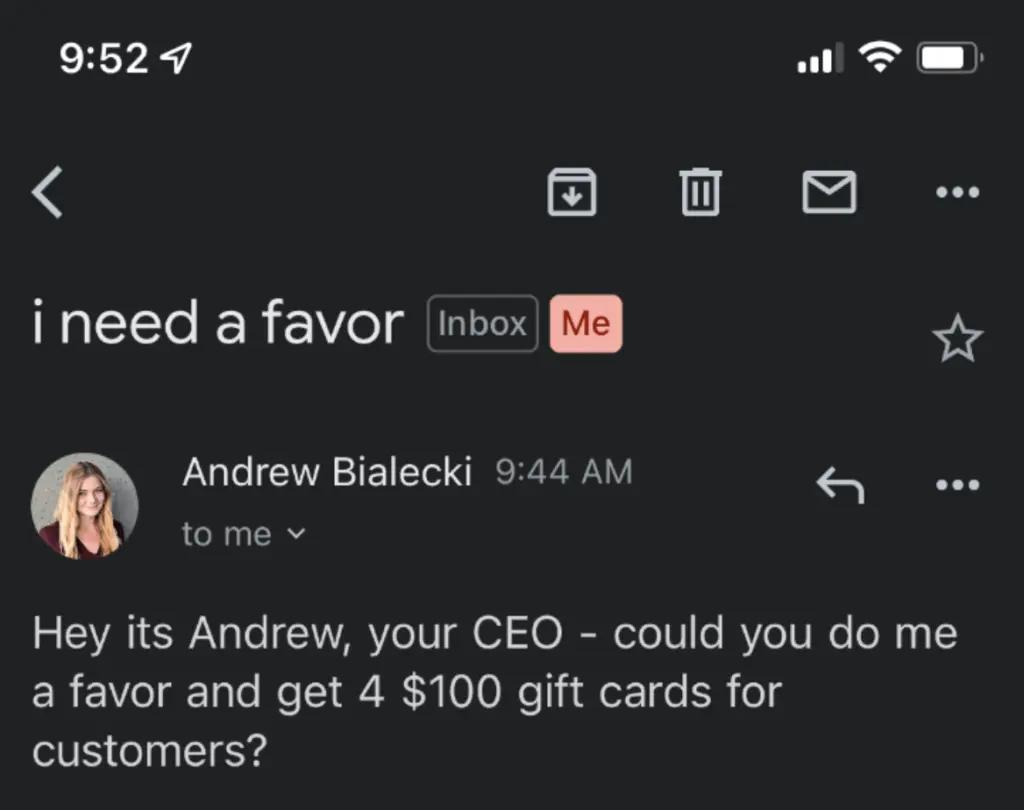
In an online diversion theft scheme, a thief steals sensitive data by tricking the victim into sending it to or sharing it with the wrong person. The thief accomplishes this by spoofing the email address of someone in the victim’s company.
Spoofing a business email address is when you send an email to someone that looks like it is from someone they work with or work for, but isn’t. We included an example of this above in the email photo title “I need a favor.”
Baiting
Baiting is a type of social engineering attack that lures victims into providing sensitive information or credentials by promising something of value for free.
For example, the victim receives an email that promises a free gift card if they click a link to take a survey. The link might redirect them to a spoofed login page that captures their email address and password and sends them to a malicious actor.
Pre-texting
Pretexting is a type of social engineering attack in which a scammer creates a pretext or fabricated scenario—pretending to be an IT administrator, for example, for a larger company—to con someone into providing sensitive business information. In this type of attack, someone can also physically acquire access to your data by pretending to be a vendor or contractor to gain your staff’s trust.
Scareware
Scareware is a form of social engineering in which a scammer inserts malicious code into a webpage that causes pop-up windows with flashing colors and alarming sounds to appear.
These pop-up windows will falsely alert you to a virus that’s been installed on your system. You’ll be told to purchase and download their security software, and the scammers will either steal your credit card information, install real viruses on your system, or (most likely) both.
Tailgating / Piggybacking
Tailgating, also known as piggybacking, is a social engineering tactic in which an attacker physically follows someone into a secure or restricted area. Sometimes the scammer will pretend they forgot their access card, or they’ll engage someone in an animated conversation on their way into the area so their lack of authorized identification goes unnoticed.
Watering hole
In a watering hole attack, a hacker infects a legitimate website that their targets are known to visit. Then, when their chosen victims log into the site, the hacker either captures their credentials and uses them to breach the target’s network, or they install a backdoor trojan to access the network.
How to protect yourself and your team from social engineering attacks
So, what can you do to make sure your team avoids these kinds of attacks?
Read email and text message carefully
There are several ways to identify a socially engineered attack from the get-go, you just have to remember to look for them.
Here’s a good list:
- Mismatched links: Make sure the link you’re clicking on is the same as the hyperlink provided. Do this by hovering over the hyperlink to see if the two match. If they don’t, it’s probably a phish.
- Unexpected hyphens, display names, incorrect spelling, and more: Bad actors who are trying to mimic aliases often use hyphens, display name spoofing, or incorrect spellings in email addresses. Consider, for example, your.CEO@hotmail.com or HR@klaviy0.com. In the first example, the attacker uses your CEO’s real name, but the domain is a free email provider instead of your company’s domain. In the second example, the “o” in Klaviyo has been replaced with a “0”.
- Suspicious senders: It’s always a good idea to double check the address a message was sent from. Ask yourself: Was I expecting to hear from them? Have I received an email from this sender before? Has the formatting been similar?
- A sense of urgency: Bad actors often try to incite fear and stress in the hopes you won’t look too closely at the errors in the message. Messages like these are trying to push you into fight-or-flight mode so that you’ll panic enough to click on their fraudulent message. They may try to tell you: That someone has accessed your account, To re-set your password in a short window of time or you’ll be locked out, To verify personal information for payroll accuracy, That your manager is requesting a gift card ASAP.
- Requests to log in to your online platform: A bad actor may send you a fraudulent link, disguised as a request to log in to your marketing automation platform, your bank, your social media account—you name it. The attacker’s goal, here, is to encourage you to navigate to a fake, malicious site designed to collect your username and password. They then run automations testing the same username and password against banking sites, social platforms, email providers, and more. Always use your SSO tool or the homepage of the platform you’re trying to access And never re-use passwords from account to account.
- Requests to open an attachment: Bad actors often include attachments to their emails. The attachments are designed to install malware that, if opened, are capable of damaging your data or stealing your information. Ask yourself: Was I expecting this attachment? Have I received an email from this sender before let alone an attachment?
Remember, attackers are going to create a sense of urgency!
Protect yourself with unique, strong passwords and multi-factor authentication
One of the most common threats to businesses according to the Verizon Data Breach Report is the use of stolen credentials: “Attackers can get your credentials (username and password) via many different methods.
- Brute force attacks (where attackers use automation to try numerous combinations of letters, symbols and numbers to guess your credentials)
- Various types of malware (thus the value of having an up-to-date Antivirus)
- Reused passwords from another site that has been hacked and last but not least, social attacks such as Phishing.”
Knowing this, you can protect your company, team and your online accounts by ensuring you use strong, unique passwords for all your web properties and to set up multi-factor authentication (MFA).
What is a strong unique password?
A strong, unique password is exactly what it sounds like: It is a long password (typically 12 characters or more) that does not use common words or phrases, cannot be socially engineered back to you (like using your initials and your wedding date), and one that isn’t recycled or reused across various accounts.
Strong, unique passwords significantly reduce how far a hacker can go if your credentials are stolen.
What is multi-factor authentication (MFA)?
MFA operates under the concept of “something you know (e.g. username and password)” and “something you have (e.g. one time passcode generated by an authenticator app)”.
So, if an attacker has knowledge of your username and password, they will also need that second factor to access your accounts.
Similar to MFA, Klaviyo gives customers the option to use two-step authentication (2FA), and enabling it helps make your account more secure.
How you can protect your Klaviyo account
Klaviyo has several built-in features you can use right now to help protect your account. Here are our top recommendations to keeping your account secure.
Review user access and permissions regularly
Regularly performing user access reviews—to ensure an employee’s account permissions are commensurate with their job responsibilities—is crucial. In this process, you may revoke access from anyone who doesn’t need it anymore or who has left the company.
Companies perform user access reviews to reduce risk and help make sure that access to systems and data is restricted to authorized and active personnel. A typical cadence for these reviews is every 90 days, though it depends on your business risk appetite.
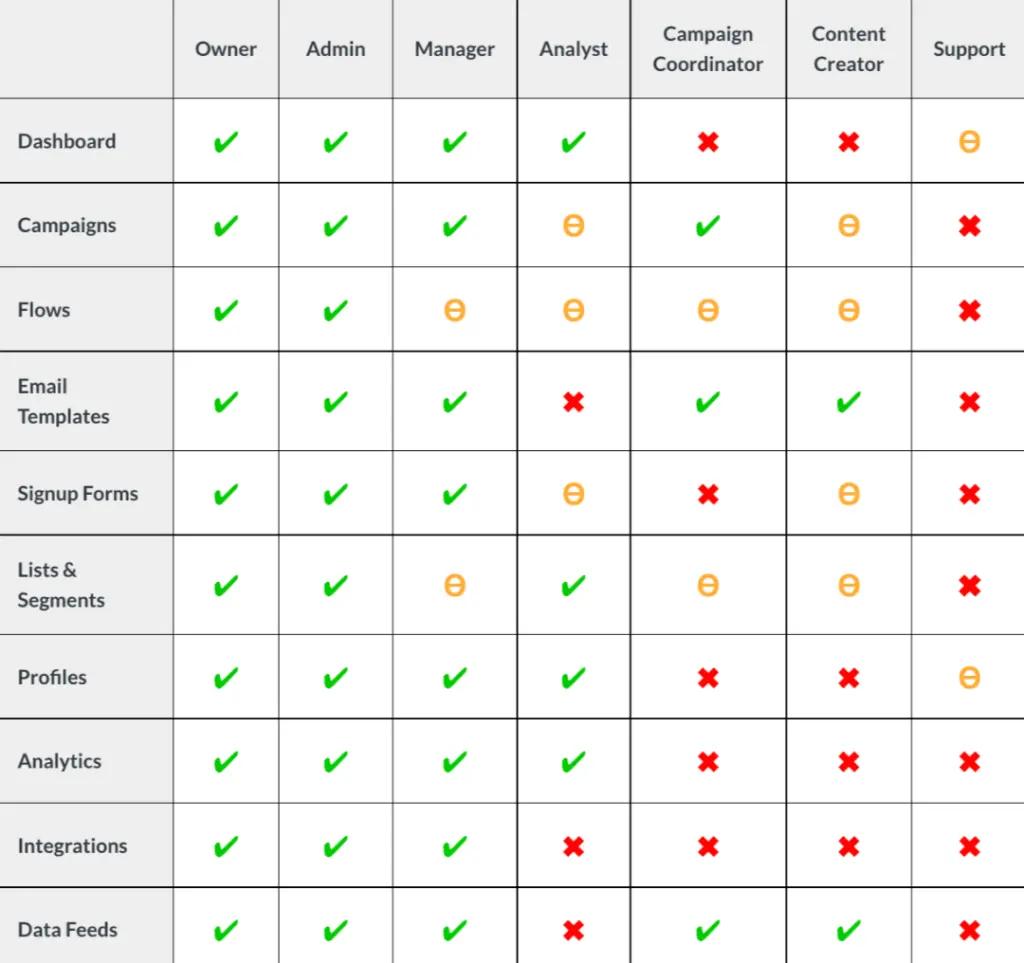
Our product offers various roles as evidenced in the table below and permissions vary, with some having more access than others. A user access review is a perfect opportunity to make any adjustments to better align access permissions with a user’s role within your organization.
Ask yourself these questions when performing a user access review:
- Are they an active employee?
- Do all users require access to the business account?
- Do all users have the proper access permissions (owner, admin, etc.)?
- When did a user last authenticate the account? (If they haven’t authenticated in a while, they may no longer need access.)
Protect your private API keys
While it’s OK to expose your public API key (which is a unique identifier, but can’t be used to access data in your Klaviyo account), your private API keys can be used to manipulate some sensitive data including modifying lists and segments, downloading full lists, deleting profiles, creating and updating campaigns, among other capabilities.
To avoid the sharing of your private API keys, make sure you and your team:
- Treat your private key like a password. Only share it with a person or party you trust.
- Name your private key so you can easily find, delete, and re-create the key if it gets compromised.
- Consider who has access to create or change API keys. It’s standard for managers, administrators, and owner roles to have this ability.
- Rotate your API keys after a team member who had access to the private key leaves the company.
Finally, here are a few things you should never do with your private API key:
- Expose your private key in a public space.
- Share your private key via email or direct message.
- Enter your private key directly into your source code via typing or hardcode.
Enable 2FA in Klaviyo
If you are an administrator within your Klaviyo account, you have the power to enforce 2FA for your entire company. If you’re an end user, you can set this up on your own.
Klaviyo: the tool to keep your and your customers’ data private
Klaviyo allows you to collect and store customized fields of information on your customers. This can be incredibly useful when sending personalized emails and text messages.
But in a day when privacy is front and center, it’s important to not only take steps to protect your company and Klaviyo account as identified above, but to ensure you have good hygiene to meet global privacy requirements.
Data minimization: the many benefits of following the principle
Data minimization is a principle that says the organization controlling the data should limit the collection of personal information to only what is directly relevant to accomplish a specific purpose.
Lauren Worcester, senior GRC analyst at Klaviyo, recommends that you lead with this principle. Here’s why:
- Data privacy compliance: It’s easier for your company to manage your data privacy compliance as both the US and the world move toward more privacy-focused laws. Both the US and UK GDPR specifically outline data minimization as a principle that should be followed. It also helps in fulfilling any data subject requests.
- Security events: In the event of a data breach or security incident, the less data that is potentially exposed, the better—especially if your data sets don’t include any sensitive information.
- Effective data: If you implement data minimization and audit the fields you can collect, you can also reduce the risk where you’re collecting sensitive or personally identifiable information.
Worcester shares an example of effective data: “If you want to collect customer birthdays to send them a birthday flow, consider whether you need to know the year, or if you can achieve the same outcome with only days and months.”
Learn more about how to comply with data protection regulations when marketing with Klaviyo.
Final thoughts
With cyberattacks increasing and privacy laws strengthening, it’s important to stay on top of every aspect of cybersecurity. Klaviyo is here to help you do that.
Ready to secure your account more effectively?
Set up 2FA today